High Orbit Ion Cannon Original
Mar 23, 2015. There's a tool for exporting to github but the controller source is an old version and not worth keeping, however The documentation is a bit of a different matter. There's not too many sources out there which describe the N64 controller protocol and I thought it might be a good idea to rewrite my documentation. N64 controller pc. There are tutorials out there for using an NES controller with an Arduino, but using the more complicated N64 controller and its analog joystick has a definite. It simply queries the N64 controller for data on the buttons and Analog stick and sends it back to the computer over the serial port. It is easy enough to modify,. CS150 Project. Checkpoint 1. Dreamkatz Controller Interface. 1.The N64 Controller. Physical interface. Communication protocol. Design structure and FSM. Serial data input. Imagine the waveform going into your flipflops are all shifted in time! Communication between devices running on different.
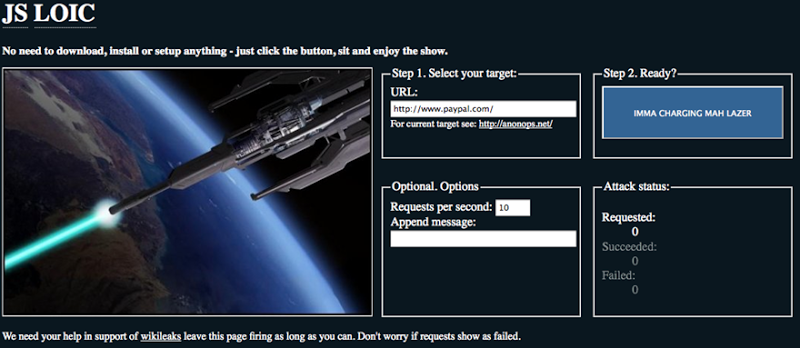
High Orbit Ion Cannon

Contents.UseLOIC performs a (or when used by multiple individuals, a DDoS attack) on a target site by flooding the server with or packets with the intention of disrupting the service of a particular host. People have used LOIC to join.The software inspired the creation of an independent version called JS LOIC, as well as LOIC-derived web version called Low Orbit Web Cannon. These enable a DoS from a. CountermeasuresSecurity experts quoted by the BBC indicated that well-written rules can filter out most traffic from DDoS attacks by LOIC, thus preventing the attacks from being fully effective. Specifically, it has been claimed that filtering out all and traffic helps to effectively address LOIC attacks.
Because internet service providers provide less bandwidth to each of their customers in order to provide guaranteed service levels for all of their customers at once, firewall rules of this sort are more likely to be effective when implemented at a point upstream of an application server's internet uplink. In other words, it is easy to cause an ISP to drop traffic destined for a customer by sending a greater amount of traffic than is allowed on that customer's link, and any filtration that occurs on the customer side after the traffic traverses that link will not stop the service provider from dropping excess traffic destined for that customer.LOIC attacks are easily identified in system logs, and the attack can be tracked down to the IP addresses used at the attack.

Notable uses Project LOIC and 4chanLOIC is the result of a brainstorming between hackers on 4chan in 2004, they sought to create a simple and efficient tool for a future cyberwar. Once the concept of simultaneous connection request architecture was set up it took few months to create it. Its existence became known much later to the public. Project Chanology and Operation PaybackLOIC was used by during to attack websites from the Church of, once more to (successfully) attack the 's website in October 2010, and again during in December 2010 to attack the websites of companies and organizations that opposed. Operation Megaupload. Main articles: andIn retaliation for the shut down of the file sharing service and the arrest of four workers, Anonymous DDoSed the websites of UMG (the company responsible for the lawsuit against Megaupload), the United States Department of Justice, the United States Copyright Office, the Federal Bureau of Investigation, the MPAA, Warner Brothers Music and the RIAA, as well as the HADOPI, all on the afternoon of January 19, 2012, through LOIC.
Origin of nameThe LOIC application is named after the, a fictional weapon from many sci-fi works, and in particular after its namesake from the series of video games. See also.References.





